Post LastPass Breach - Real Consequences, Real Lessons
LastPass was breached, and your passwords may be compromised. But password managers are still critical for security, in both personal and professional settings.

I ran across this article showing that just under one year on it seems that the LastPass breach is being used to access crypto assets of a number of users. And while the article does a fine job of discussing the issues, I think there is more to be said. My thoughts are for both individuals and for those businesses who use password managers to store common admin passwords and other sensitive data.
Password Managers Are Critical
So live, as of this moment, I have over 210 logins (passwords) stored in my password manager. In my work provided one, I have over 80. Many of these passwords include over 20 characters each. And I've only reused passwords on 13 of them - which means they were passwords I had created/used that I migrated into my password manager, and that I was a bit sloppy in my "youth" with not reusing passwords)
If I tried to manually create passwords for the nearly 300 different systems I log into, and then remember those - especially for sites I don't log into more than once in a blue moon - I would have a bunch of weak passwords, a bunch of them reused across multiple sites, and a bunch of frustrating "please reset my password" events. It just isn't practical to manually manage your passwords these days.
Now, the good news here is that you can't throw a stone without hitting a comparison review of password managers, and a simple web search can net you a bunch of results, like these: review 1, review b, review iii, review quatro.
Key Features For Your Password Manager
So as you're reading these reviews, keep these ideas in mind:
- Multi-platform support. Will it work on your iPhone? How about that Chromebook? Your Linux desktop? (Don't you judge me!) How about Windows 11? Which browsers does it support?
- Password sharing capability. I share hundreds of passwords with my family - like those for certain financial accounts, for subscription services, and many others. But I also keep others private from them. This is a really important feature for both families and small (or even larger) businesses.
- Easy import of existing password databases from other services. (and, conversely, easy export).
You may note that "security" wasn't one of my bullet points. Neither was price. That's for a few reasons. Any of the password managers recommended by a reputable platform - like the ones I linked to - are going to be reasonably secure. (NOTE: reasonable does not mean 100% hackproof - just as there is no such thing as a 100% tornado proof Kansas farmhouse, or a 100% hurricane proof Carolina beach house: these are idealized fantasies that don't exist in the real world) As for price, you will find that there are good free options as well as good paid options, so choose as per your needs and concerns.
What a Password Manager Really Buys You: Time
I know, you thought they got you things like encryption, ease of use, and protection. And, well, yes, they do. But that really does all boil down to time. Using a complex password means that adversaries will take longer to brute-force "guess" your passwords at sites like your bank. Encrypting your password vault with strong encryption means that anybody who somehow gets their hands on your password vault file will take a bunch of time trying to decrypt it to get to your passwords.
Everything else is a "nice to have," yet these nice to have features are the ones you're really making your purchasing decision based on.
Don't believe me? Well check out these two charts from Hive Systems, for 2022 and 2023 respectively:

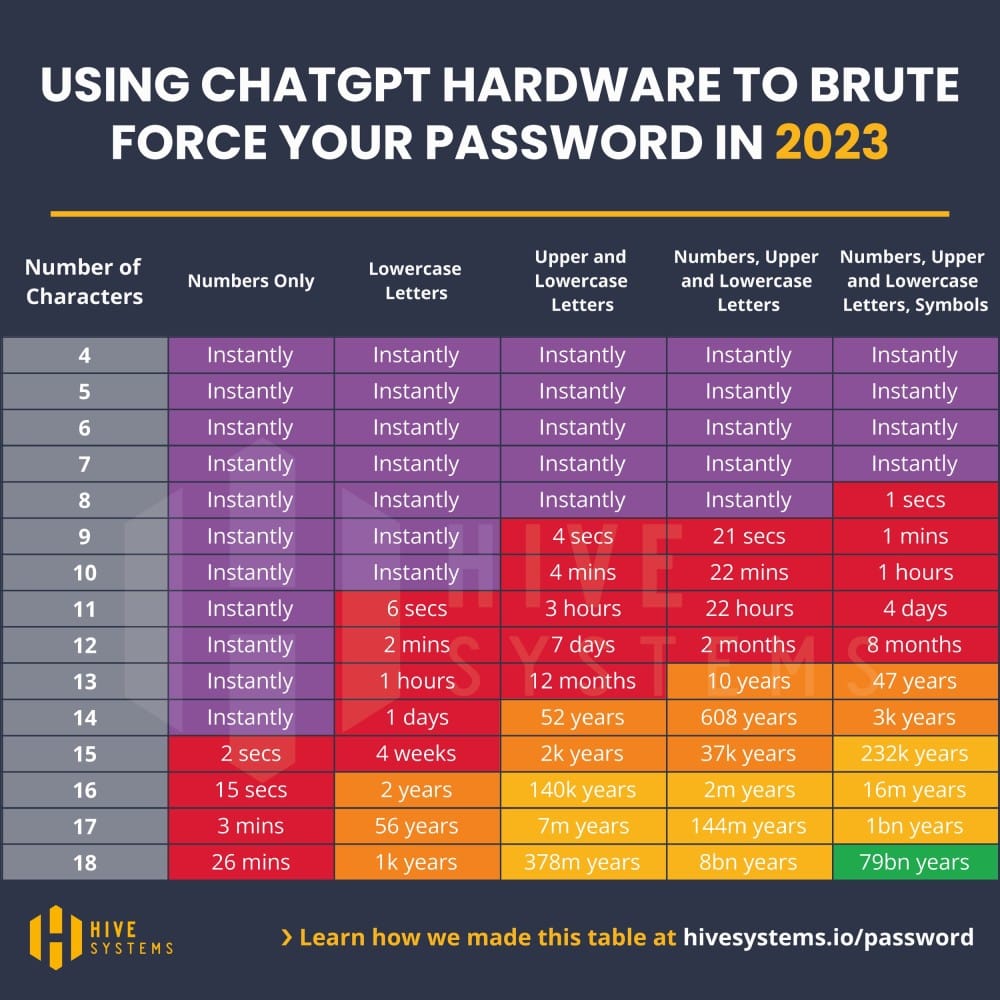
Protecting Your Passwords Against the Ravages of Time
Getting back to that article that peaked my interest: we're seeing that within a few months of the LastPass breach, some "well protected" crypto currency accounts started getting drained. The long and the short of it seems to be that the encryption protecting LastPass password vaults was able to buy people months of post-breach protection, but unfortunately many people didn't use that time to their advantage. Since Doc Brown isn't mass-producing time machines, we have to use the time we have wisely.
If Your Password Manager Gets Hacked
Time is of the essence. Your encrypted vault should be assumed to be in the hands of ne'er-do-wells. Assume they're prepared to start the work of decrypting your vault to see what interesting accounts of yours they can start to access. Assume that they may simply sell off your info to someone else who might have an even better plan for what to do with your data. In the first 2 weeks post breach, I recommend you take the following steps:
- Make a determination as to if you need to change password managers. Just because they got breached doesn't mean you should just blindly switch. (sad, but true) Spend a bit of time looking at the coverage, and seeking out opinions of reputable security voices.
- Change every password stored in your vault. If you store your multi-factor tokens in your vault as well, change those too. I know, this sounds like a daunting task, but consider that this is the ounce of prevention that will stop you from possibly needing the pound of cure for when your crypto wallet or bank account gets drained.
- In social media and other systems that keep you logged in on multiple devices for an extended time, use the app/website for that service to force log-out all your instances and manually log back in.
Preparing For a Password Manager Breach
Getting caught in a rainstorm is usually better when you're prepared with an umbrella or a raincoat - or on extremely hot days perhaps your swimsuit. So, true, it is advantageous to take some steps to prepare yourself for password manager breaches.
- Enable multi-factor auth for every account you are able to. Even the relatively poorly secured SMS based MFA is better than nothing. Most situations where MFA is enabled for consumer accounts (your bank, for example) only require MFA for sign-on from new systems, or once every blue moon or so, which means you're not really inconveniencing yourself at login time.
- Change the passwords for your important sites regularly. Yearly could be a worthwhile strategy. Let's face it, you probably still have some passwords that you've imported into your password manager that are the equivalent of "qwerty123!" and are just begging to be guessed. You may also have passwords from a few years ago when recommendations were that 10 character passwords were sufficiently complex to thwart brute force attacks. That guidance changes almost yearly at this point, and you should upgrade your passwords to match.
A Passwordless Future
Look, I'm excited for this concept. Imagine putting an end to "I forgot my password," and "but I thought 'mm-dd-yyyy-Name' was a good password!" I think it is more likely we'll see a "LessPassword" future. Passkeys, tokens, certificates, and others are all viable solutions. Biometrics may become more powerful and more common. But passwords are here to stay for some time, we need to be smart about how we use them and how we think about the tools we use to help us manage them.
Originally published on LInkedIn September 6, 2023
